By Catalin Cimpanu
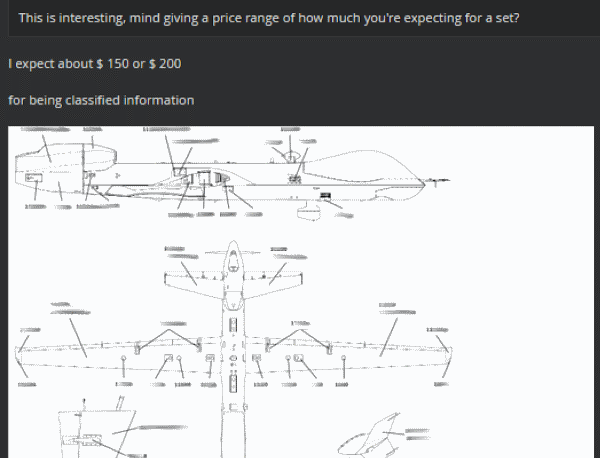
 A hacker is selling sensitive military documents on online hacking forums, a security firm has discovered. Some of the sensitive documents put up for sale include maintenance course books for servicing MQ-9 Reaper drones, various training manuals describing comment deployment tactics for improvised explosive device (IED), an M1 ABRAMS tank operation manual, a crewman training and survival manual, and a document detailing tank platoon tactics. Hacker asking between $150 and $200 for the lot
A hacker is selling sensitive military documents on online hacking forums, a security firm has discovered. Some of the sensitive documents put up for sale include maintenance course books for servicing MQ-9 Reaper drones, various training manuals describing comment deployment tactics for improvised explosive device (IED), an M1 ABRAMS tank operation manual, a crewman training and survival manual, and a document detailing tank platoon tactics. Hacker asking between $150 and $200 for the lot
US-based threat intelligence firm Recorded Future discovered the documents for sale online. They say the hacker was selling the data for a price between $150 and $200, which is a very low asking price for such data.
Recorded Future says it engaged the hacker online and discovered that he used Shodan to hunt down specific types of Netgear routers that use a known default FTP password. The hacker used this FTP password to gain access to some of these routers, some of which were located in military facilities, he said.
Based on the documents and details he shared online and with researchers in private conversations, one such location was the 432d Aircraft Maintenance Squadron Reaper AMU OIC, stationed at the Creech AFB in Nevada.
Here, he used access to the router to pivot inside the base's network and gain access to a captain's computer, from where he stole the MQ-9 Reaper manual and a list of airmen assigned to Reaper AMU.
MQ-9 Reaper drones are some of the most advanced drones around and are used by the US Air Force, the Navy, the CIA, the Customs and Border Protection Agency, NASA, and the militaries of other countries.

The hacker didn't reveal from where he stole the other documents, but based on the information they contain experts believe that they were most likely taken from the Pentagon or from a US Army official.
"While such course books are not classified materials on their own, in unfriendly hands, they could provide an adversary the ability to assess technical capabilities and weaknesses in one of the most technologically advanced aircrafts," Andrei Barysevich, Director of Advanced Collection at Recorded Future said.
Incident caused by use of router default FTP credentials
The incident could have very easily been prevented if the military base's IT team would have followed best practices and changed the router's default FTP credentials..
The issue with Netgear routers using a set of default FTP credentials is known since 2016 when a security researcher raised the alarm about it. Netgear responded by putting up a support page with informationon how users could change their routers' default FTP password.
Recorded Future said that at the time of writing, there are more than 4,000 such routers (Netgear Nighthawk R7000) available online via "smart device" search engines like Shodan.
The hacker also bragged about accessing footage from an MQ-1 Predator flying over Choctawhatchee Bay in the Gulf of Mexico. This isn't something new, though, as the US government agencies have been known to leak those feeds once in a while.
Recorded Future said it reported the finding to US authorities, which are now investigating the hacks. Researchers hinted at also discovering the hacker's country of origin, albeit they did not make the information public.
No comments:
Post a Comment