By David Hambling
The Decade, Reviewed looks back at the 2010s and how it changed human society forever. From 2010 to 2019, our species experienced seismic shifts in science, technology, entertainment, transportation, and even the very planet we call home. This is how the past ten years have changed us.
The 2010’s saw a step change in cyber warfare, defined as attacks against a nation by a computer. Rather than just being used for spying, this was the decade the digital world was weaponized to break through to the physical.
Analysts had long warned about the potential for cyber operations. Now, malware has attacked machinery, power grids, and military control systems and brought a new dimension to warfare.
This is how cyberwarfare came of age in the 2010s.
A Long List of Cyber Skirmishes
In 2010, the Stuxnet worm targeted Iranian nuclear facilities. This was no ordinary piece of malware, but the product of what political scientist P.W. Singer called “a Manhattan Project-like” effort, by unknown actors.
Stuxnet infected logic controllers running industrial machinery, specifically targeting centrifuges used for enriching uranium. The malware made the centrifuges spin out of control and tear themselves apart, severely disruption Iran’s nuclear program.
Soon this kind of Cyber Coercion became an established technique for applying strategic political pressure. In March 2013, simultaneous attacks on six of South Korea’s financial institutions damaged 32,000 computers. The attacks came at a time of heightened tension with North Korea. It wouldn't take long for the South Korean government to trace those attacks to Pyongyang.
And it wouldn't be the last time South Korea would be the victim of a cyber attack. After deploying the U.S. THAAD missile defense system in 2016, China loudly denounced the move, applying economic pressure and unleashing a series of cyber attacks. The Chinese military term for this sort of campaign is “weishe” (威懾), which can be translated as either “deterrence” or “compellence.” While it failed to persuade South Korea to drop THAAD, it gave a taste of what China is prepared to do—unofficially, of course—in support of its policies.
Cyber warfare also bled into traditional battlefields. In 2014 Ukrainian artillery officers fighting Russian-backed opposition forces used an app to direct howitzer fire. The app was hacked by Russian group Fancy Bear, and an infected version was distributed with embedded spyware. The spyware gave away the users' location, and Ukrainian officers found their positions coming under highly accurate enemy fire guided by the hijacked app.
But if Russia has cyber skills, so too does the United States. After a U.S. drone was shot down over the Strait of Hormuz in June 2019, President Trump called off airstrikes against Iran due to risk of casualties. But that didn't stop the U.S. from immediately hitting Iranian missile and rocket forces with its own cyber attack, putting them out of action for an unknown length of time.
A Utility Vulnerability

A blackout in Ukraine in 2015.
MAX VETROVGETTY IMAGES
Shutting down the power grid via cyber attack has long been the stuff of techno thrillers and media scare stories, but the nightmare became real in 2015 when BlackEnergy malware hit Ukrainian electricity supplies, leaving over 200,000 people without power.
The attack, allegedly carried out by Russia, affected the SCADA (Supervisory Control and Data Advisory) system which controls distribution, disconnecting substations from the grid. It could only be overcome by switching to manual control.
The BlackEnergy incident is the first known case of a cyber attack taking down power distribution, but it will surely not be the last. Security agencies report that Russia has made intrusions into the U.S. energy infrastructure since 2016. They may even be behind attacks this September. While the attacks didn't cause any outages, they did cause "blind spots" for grid operators for about half a day. The electricity kept flowing, but it was a wake-up call that such systems aren't as safe as previously thought.
Democracy In the Crosshairs
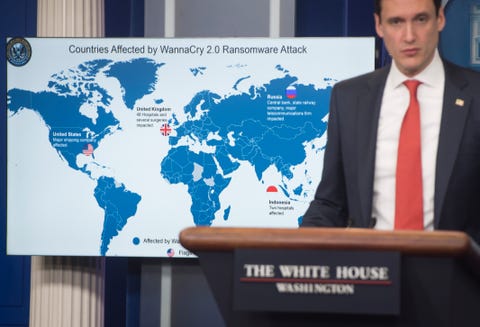
SAUL LOEBGETTY IMAGES
But the attacks that grabbed the most headlines came from malware attacks, often perpetrated by intelligence agencies using cybercrime to cloak activities.
Ransomware, a type of malware which locks up a computer and encrypts data so the user can only get their information back by paying off the attacker, has been around for a while. But in 2017, there were three particularly damaging ransomware vectors: Petya, NotPetya, and Wannacry. All were closely related, and a White House official described NotPetya as "the most destructive and costly cyber attack in history."
Strangely, the malware seemed to be corrupted, and victims could not pay the ransom even if they tried. But the twist came when the software was revealed to be a sabotage tool masquerading as ransomware. Eventually, the NSA pointed the finger at Russia though, ironically, the ‘exploit’ which it was based on had been previously discovered by the NSA itself.
Similarly, an attack in 2018 which hijacked details of some 500 million people from the Marriott Hotel’s data stores looked like the work of criminals. But the intrusion was traced to a Chinese intelligence agency, apparently as part of their efforts to sweep up data to target significant individuals.
The 2010s was also the decade when democracy itself came under attack from the internet. Russia in particular has been identified as the source of covert meddling in elections, and increasing numbers of Russian chatbots have been identified pushing Putin’s agenda on social media around the world.
These machines are supplemented by an army of humans at Russia’s "troll factory" – officially the Internet Research Agency in St Petersburg—where staff are paid to engage in online discussions in blogs and comments sections, repeating arguments and spreading disinformation. The IRA even have their own fake blogs and news sites, backed by software to generate large numbers of post views toma boost their rankings.
The full impact of this interference, and direct cyberattacks such as those directed at voter registration in several U.S. states, has yet to be established.
Up Next: A Growing Threat

Military operations during Cyber Blitz 2019, an exercise for practicing cyber operations.
ERIC THOMPSON
Considering all this unseen digital malfeasance, the U.S. military finally got serious about cyber warfare in the 2010s.
Cyber Command (aka USCYBERCOM), a tiny outfit in 2010, achieved the status of a unified combatant command led by a four-star general in 2017. This puts it on a level with Strategic Command, which co-ordinates nuclear forces. USCYBERCOM similarly draws together Army, Navy, and Air Force elements (as well as Marine Corps and Coast Guard) and now has more than 6,000 personnel in 133 teams.
USCYBERCOM was initially conceived as being used for defense but can now carry out a full spectrum of military cyberspace operations, includes offensive measures. Naturally, its capabilities are secret and its operations are not disclosed. But some details are known such as Operation Glowing Symphony, a successful campaign against ISIS that brought down the terrorist group’s media operation, taking out websites, mobile apps, and communications.
Increasingly, the military see cyberspace as an additional ‘domain’ alongside air, land, and sea. But it's a battlefield where skirmishes are fought without war ever being declared, and an adversary never fully known.
Any future war is likely to include cyber attacks as well as physical ones. In many ways, the 2010s for cyber feel like what the 1910s were for aviation during WW1. While air forces made up only a tiny section in the U.S. Army before the Great War. it rapidly grew until it became key aspect of modern warfare by mid-century.
In a couple decades, cyber warfare might become the deciding factor between who wins and who loses.

No comments:
Post a Comment