On October 29, authorities at the Kudankulam Nuclear Power Project (KKNPP), in Tamil Nadu, issued a statement denying (Image 1) the speculation of a cyber incident at the power plant. The Indian Express reported senior government officials saying that an audit had ‘confirmed that an “incident” had occurred (in early September), though not to the main operations of the plant’. The accumulated evidence, however, tells a far more disturbing story, albeit circumstantial, and the KKNPP denial raises more questions than it answers.
There are three pieces of circumstantial evidence that point to a significant cyber event having taken place.
First, as per publically available documents, the fact that the Nuclear Power Corporation of India (NPCIL) issued tenders for (and bought) Windows systems. This shows that there were several Windows-enabled computers operational within the KNPP air gap. As cyber expert Samuel Cardillo told me in an interview, in any nuclear power plant the administrative side is neatly separated from the operations side for security reasons. If indeed Windows was only used in the administrative side, this raises the question as to what was the operating system (OS) used on the operations side? The only alternative explanation is that the operations of the plant were run on an OS developed ab-initio by India exclusively for use by India.
This begs the question: What is this OS based on and how long did it take to integrate the said system with Russian equipment which would add a whole new layer of complexity (and vulnerability in addition to malfunction) to an already complex system. It is important to note that the virus in question ‘DTRACK’ is programmed to attack Windows operating systems.
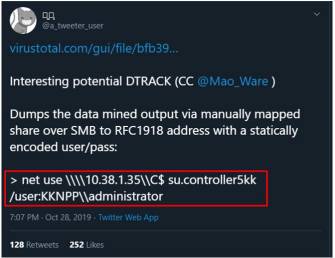
Second, we know for a fact from the Kudankulam data dump that KKNPP had a MyStub.exe file. Cardillo explains this as ‘the camouflage on a Trojan horse’ or to use an Indian context, it's like finding a file in a defence ministry computer titled AlJihadAlHind.exe, which should have immediately raised a red flag. He explains a stub as ‘an encrypted file that allows the virus to remain undetected — an embryo of sorts — a virus nursery that helps the virus regenerate and renew itself while staying hidden.... the fact that it was labelled MyStub should have in itself sent alarm bells ringing’. Importantly, the data dump image below shows administrator access. (Image 2)
Third, the fact that the plant has suffered multiple shut downs suggests a serious and persistent equipment problem. In many ways this is reminiscent of the Stuxnet attack on Iran, which over time, significantly reduced the efficiency of Iranian centrifuges causing them to malfunction regularly.
This is hardly surprising given that the progenitor of DTRACK, was a ransom-ware system that had infiltrated Sony for over two years but stayed latent collecting information and played its hand only much later. In that sense it is impossible to tell when the virus was implanted (if it was implanted) and when it would start acting up. Certainly, the frequent failures at KKNPP point to a Stuxnet-style gradual attrition of capability. If this is not malware related, this points to a possibly more serious design problem.
Image 2; Shows administrator access
 Absent in this (and KKNPP's official denial) is the discussion of India's security culture — that is to say the human angle. What one should remember is that it is a scrupulous adherence to data hygiene that prevents the breaching of an air gap. To date we have had repeated breaches of Ministry of External affairs computers by Chinese hackers (including highly sensitive data).
Absent in this (and KKNPP's official denial) is the discussion of India's security culture — that is to say the human angle. What one should remember is that it is a scrupulous adherence to data hygiene that prevents the breaching of an air gap. To date we have had repeated breaches of Ministry of External affairs computers by Chinese hackers (including highly sensitive data).
Also to note that the Natanz nuclear facility was not attacked via networks, but rather through a lax security culture where contractors were allowed to use private USB sticks within the Natanz air gap. To note, that some of these contractors also used these USB sticks in India, and transferred the virus to several Indian facilities.
Notably, unlike in the United States, where 2 per cent of nuclear programme staff are laid off every year for minor infractions (sometimes not even related to their work, such as a repeat occurrence of speeding tickets or gambling problems), we still have no transparency with regards to our personnel reliability programme.
In short, if indeed a breach has occurred, it is a human problem not a network one and KNPP's diagnostic and denial does little to restore confidence.


No comments:
Post a Comment